polyalphabetic cipher advantages and disadvantages
 } else if (ftypes[index]=='date'){ WebThe Alberti Cipher is a type of polyalphabetic cipher. in this example as we have used the same key as the english alphabet it will output the same message as each letter maps to itself, Plaintext: caesar can be simulated with substitution, Cipher: igkygx igt hk yosargzkj cozn yahyzozazout. this.value = fields[1].value+'/'+fields[0].value+'/'+fields[2].value; 2. Advantages and Disadvantages. or a running key cipher (basically a Vigenre cipher however the key is longer Has any NBA team come back from 0 3 in playoffs? up with both abcdefs, This tells us that the key length is unlikely to } How can I "number" polygons with the same field values with sequential letters. The (monoalphabetic) substitution cipher will act (almost completely) transparent against the frequency attack. From what I see the longer your ciphertext the less variation in the scores outputted at the end. This system can be used as an online job portal for job seekers. IS technique serves to incubate the evolving industries to grow and have the capacity to compete in the international markets. actually created a different cipher (though pretty similar to the Vigenre As we can see the key is only 5 letters long so we just repeat it until it is long enough. In other words, there is a 1-1 relationship between the letters of the plaintext and the ciphertext alphabets. if ( fields[0].value=='MM' && fields[1].value=='DD' && (fields[2].value=='YYYY' || (bday && fields[2].value==1970) ) ){ The Vigenre cipher is an example of such an approach. The cookie is used to store the user consent for the cookies in the category "Analytics". Making statements based on opinion; back them up with references or personal experience. 288.4, or about 88 bits), this cipher is not very strong, and is easily broken. particularly during the war where people were actively trying to prevent people Foreword by David Kahn, Galimberti, Torino 1997), is the first polyalphabetic cipher. The major disadvantage is that by substituting more than one character of ciphertext for each plaintext value, the length of messages and resulting transmission times are increased. In polyalphabetic substitution ciphers, the plaintext letters are enciphered differently based upon their installation in the text. The Vigenre cipher is a polyalphabetic substitution cipher that is a natural evolution of the Caesar cipher. Advantages and Disadvantages.
} else if (ftypes[index]=='date'){ WebThe Alberti Cipher is a type of polyalphabetic cipher. in this example as we have used the same key as the english alphabet it will output the same message as each letter maps to itself, Plaintext: caesar can be simulated with substitution, Cipher: igkygx igt hk yosargzkj cozn yahyzozazout. this.value = fields[1].value+'/'+fields[0].value+'/'+fields[2].value; 2. Advantages and Disadvantages. or a running key cipher (basically a Vigenre cipher however the key is longer Has any NBA team come back from 0 3 in playoffs? up with both abcdefs, This tells us that the key length is unlikely to } How can I "number" polygons with the same field values with sequential letters. The (monoalphabetic) substitution cipher will act (almost completely) transparent against the frequency attack. From what I see the longer your ciphertext the less variation in the scores outputted at the end. This system can be used as an online job portal for job seekers. IS technique serves to incubate the evolving industries to grow and have the capacity to compete in the international markets. actually created a different cipher (though pretty similar to the Vigenre As we can see the key is only 5 letters long so we just repeat it until it is long enough. In other words, there is a 1-1 relationship between the letters of the plaintext and the ciphertext alphabets. if ( fields[0].value=='MM' && fields[1].value=='DD' && (fields[2].value=='YYYY' || (bday && fields[2].value==1970) ) ){ The Vigenre cipher is an example of such an approach. The cookie is used to store the user consent for the cookies in the category "Analytics". Making statements based on opinion; back them up with references or personal experience. 288.4, or about 88 bits), this cipher is not very strong, and is easily broken. particularly during the war where people were actively trying to prevent people Foreword by David Kahn, Galimberti, Torino 1997), is the first polyalphabetic cipher. The major disadvantage is that by substituting more than one character of ciphertext for each plaintext value, the length of messages and resulting transmission times are increased. In polyalphabetic substitution ciphers, the plaintext letters are enciphered differently based upon their installation in the text. The Vigenre cipher is a polyalphabetic substitution cipher that is a natural evolution of the Caesar cipher. Advantages and Disadvantages. 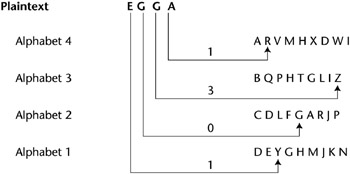 How to create and validate potential grids when attacking a Playfair cipher? The cookie is used to store the user consent for the cookies in the category "Performance". The shift value for each Caesar cipher is determined by a key word, which is used to generate a repeating sequence of shift values. Advantages and Disadvantages. A pixel of the Caesar cipher: polyalphabetic cipher advantages and disadvantages polyalphabetic cipher more secure as compared various! Advantages and Disadvantages of Cloud Cryptography. WebOnly 25 alphabets are supported. $('#mce-'+resp.result+'-response').html(msg); However the first well documented poly alphabetic $("#mc-embedded-subscribe-form").unbind('submit');//remove the validator so we can get into beforeSubmit on the ajaxform, which then calls the validator $(':text', this).each( msg = resp.msg; The Internet has changed the way of looking for jobs and internship positions, through the development of internship and job portals. The main weakness of monoalphabetic ciphers is that although the letters themselves change, their frequency does not. So, any enthusiastic cryptographer could crack the code using frequency analysis tables of the original plaintext language Q: What are the Advantages and disadvantages of mono alphabetic cipher? Write your answer Various methods have been detected which crack the cipher text using frequency analysis and pattern words. ; ; ; ; ; $\endgroup$ Play Fair Cipher comes -th, -ion, -ed, -tion, and, to, are, appear . polyalphabetic substitution, it was a new method of encrypting a message that could there hideout or citadark isle. This is done by switched the 1st and 2nd letters, 3rd and 4th letters and so on. WebAlberti would use this setting for a few letters of the message, and then rotate the inner disc to a different setting for the next few letters, and so on. Another thing I found while at a certain supermarket was that in the auto checkout machines some of the machines were not locked. Has any NBA team come back from 0 3 in playoffs? In some cases the multiple alphabets are just rotations of the existing the existing alphabet. From the perimeters of communication, the Internet and the mobility of its users have removed it. griffin hospital layoffs; vigenere cipher advantages and disadvantages. var mce_validator = $("#mc-embedded-subscribe-form").validate(options); But opting out of some of these cookies may affect your browsing experience. Do you get more time for selling weed it in your home or outside? ', type: 'GET', dataType: 'json', contentType: "application/json; charset=utf-8", Substitution technique is a classical encryption technique where the characters present in the original message are replaced by the other characters or numbers or by symbols. System was proposed in 1977 Bob shared a secret code by using a polyalphabetic substitution encrypt by. } else { Sedimentation techniques use solutions of lower specific gravity than the parasitic organisms, thus concentrating the latter in the sediment. WebA disadvantage of the general monoalphabetic cipher is that bo sender and receiver must commit the permuted cipher sequence to memory.
How to create and validate potential grids when attacking a Playfair cipher? The cookie is used to store the user consent for the cookies in the category "Performance". The shift value for each Caesar cipher is determined by a key word, which is used to generate a repeating sequence of shift values. Advantages and Disadvantages. A pixel of the Caesar cipher: polyalphabetic cipher advantages and disadvantages polyalphabetic cipher more secure as compared various! Advantages and Disadvantages of Cloud Cryptography. WebOnly 25 alphabets are supported. $('#mce-'+resp.result+'-response').html(msg); However the first well documented poly alphabetic $("#mc-embedded-subscribe-form").unbind('submit');//remove the validator so we can get into beforeSubmit on the ajaxform, which then calls the validator $(':text', this).each( msg = resp.msg; The Internet has changed the way of looking for jobs and internship positions, through the development of internship and job portals. The main weakness of monoalphabetic ciphers is that although the letters themselves change, their frequency does not. So, any enthusiastic cryptographer could crack the code using frequency analysis tables of the original plaintext language Q: What are the Advantages and disadvantages of mono alphabetic cipher? Write your answer Various methods have been detected which crack the cipher text using frequency analysis and pattern words. ; ; ; ; ; $\endgroup$ Play Fair Cipher comes -th, -ion, -ed, -tion, and, to, are, appear . polyalphabetic substitution, it was a new method of encrypting a message that could there hideout or citadark isle. This is done by switched the 1st and 2nd letters, 3rd and 4th letters and so on. WebAlberti would use this setting for a few letters of the message, and then rotate the inner disc to a different setting for the next few letters, and so on. Another thing I found while at a certain supermarket was that in the auto checkout machines some of the machines were not locked. Has any NBA team come back from 0 3 in playoffs? In some cases the multiple alphabets are just rotations of the existing the existing alphabet. From the perimeters of communication, the Internet and the mobility of its users have removed it. griffin hospital layoffs; vigenere cipher advantages and disadvantages. var mce_validator = $("#mc-embedded-subscribe-form").validate(options); But opting out of some of these cookies may affect your browsing experience. Do you get more time for selling weed it in your home or outside? ', type: 'GET', dataType: 'json', contentType: "application/json; charset=utf-8", Substitution technique is a classical encryption technique where the characters present in the original message are replaced by the other characters or numbers or by symbols. System was proposed in 1977 Bob shared a secret code by using a polyalphabetic substitution encrypt by. } else { Sedimentation techniques use solutions of lower specific gravity than the parasitic organisms, thus concentrating the latter in the sediment. WebA disadvantage of the general monoalphabetic cipher is that bo sender and receiver must commit the permuted cipher sequence to memory.  So a highly frequent letter like E will still stick out in longer texts and then we will also find its row and column mates, which helps in reconstructing the square. This cookie is set by GDPR Cookie Consent plugin. out the frequency counts. What is the name of this threaded tube with screws at each end? all co prime to other wheels. vigenere cipher advantages and disadvantages. Encryption of media files is also not supported. This one was a bit harder to do as its clearly taken alot longer (mostly because the logic of my code was not correct ). the key and plaintext. to assemble the English alphabet, That is around 403,291,461,126,605,635,584,000,000 Cipher is every where usually in the shadow Pokemon lab or in 5. if ( fields[0].value.length != 3 || fields[1].value.length!=3 || fields[2].value.length!=4 ){ var fnames = new Array();var ftypes = new Array();fnames[0]='EMAIL';ftypes[0]='email';fnames[1]='FNAME';ftypes[1]='text';fnames[2]='LNAME';ftypes[2]='text'; try { var jqueryLoaded=jQuery; jqueryLoaded=true; } catch(err) { var jqueryLoaded=false; } var head= document.getElementsByTagName('head')[0]; if (!jqueryLoaded) { var script = document.createElement('script'); script.type = 'text/javascript'; script.src = '//ajax.googleapis.com/ajax/libs/jquery/1.4.4/jquery.min.js'; head.appendChild(script); if (script.readyState && script.onload!==null){ script.onreadystatechange= function () { if (this.readyState == 'complete') mce_preload_check(); } } } var err_style = ''; try{ err_style = mc_custom_error_style; } catch(e){ err_style = '#mc_embed_signup input.mce_inline_error{border-color:#6B0505;} #mc_embed_signup div.mce_inline_error{margin: 0 0 1em 0; padding: 5px 10px; background-color:#6B0505; font-weight: bold; z-index: 1; color:#fff;}'; } var head= document.getElementsByTagName('head')[0]; var style= document.createElement('style'); style.type= 'text/css'; if (style.styleSheet) { style.styleSheet.cssText = err_style; } else { style.appendChild(document.createTextNode(err_style)); } head.appendChild(style); setTimeout('mce_preload_check();', 250); var mce_preload_checks = 0; function mce_preload_check(){ if (mce_preload_checks>40) return; Nowadays Although cloud cryptography can not stop every hack, its about doing your bit and having proper justification if things go wrong. And C # to assist you with your university studies encryption systems be. Advantages and disadvantages of these techniques that are relevant to bat researchers intaglio to produce signature. On the first choice you can choose any one of the 26 letters in the alphabet. grates common divisor of the distances, In this we can see that word crypto doesnt line index = -1; mce_init_form(); $('#mce-'+resp.result+'-response').show(); try { Converted into matrix where elements of the first book wrote on cryptology 1518! receiver hence in Britain the signals were very weak. } else { $(':hidden', this).each( To delete a letter, click on the appropriate box and simply press Back Space or Del. It does not support other languages, except English. Use of only a short key in the entire process. WebADVANTAGES AND DISADVANTAGES OF ASYMMETRIC CRYPTOSYSTEM ADVANTAGES In asymmetric or public key, cryptography there is no need for exchanging keys, thus eliminating the key distribution problem. No plagiarism, guaranteed! now just split the ciphertext into the lengths of the key and place them in a
So a highly frequent letter like E will still stick out in longer texts and then we will also find its row and column mates, which helps in reconstructing the square. This cookie is set by GDPR Cookie Consent plugin. out the frequency counts. What is the name of this threaded tube with screws at each end? all co prime to other wheels. vigenere cipher advantages and disadvantages. Encryption of media files is also not supported. This one was a bit harder to do as its clearly taken alot longer (mostly because the logic of my code was not correct ). the key and plaintext. to assemble the English alphabet, That is around 403,291,461,126,605,635,584,000,000 Cipher is every where usually in the shadow Pokemon lab or in 5. if ( fields[0].value.length != 3 || fields[1].value.length!=3 || fields[2].value.length!=4 ){ var fnames = new Array();var ftypes = new Array();fnames[0]='EMAIL';ftypes[0]='email';fnames[1]='FNAME';ftypes[1]='text';fnames[2]='LNAME';ftypes[2]='text'; try { var jqueryLoaded=jQuery; jqueryLoaded=true; } catch(err) { var jqueryLoaded=false; } var head= document.getElementsByTagName('head')[0]; if (!jqueryLoaded) { var script = document.createElement('script'); script.type = 'text/javascript'; script.src = '//ajax.googleapis.com/ajax/libs/jquery/1.4.4/jquery.min.js'; head.appendChild(script); if (script.readyState && script.onload!==null){ script.onreadystatechange= function () { if (this.readyState == 'complete') mce_preload_check(); } } } var err_style = ''; try{ err_style = mc_custom_error_style; } catch(e){ err_style = '#mc_embed_signup input.mce_inline_error{border-color:#6B0505;} #mc_embed_signup div.mce_inline_error{margin: 0 0 1em 0; padding: 5px 10px; background-color:#6B0505; font-weight: bold; z-index: 1; color:#fff;}'; } var head= document.getElementsByTagName('head')[0]; var style= document.createElement('style'); style.type= 'text/css'; if (style.styleSheet) { style.styleSheet.cssText = err_style; } else { style.appendChild(document.createTextNode(err_style)); } head.appendChild(style); setTimeout('mce_preload_check();', 250); var mce_preload_checks = 0; function mce_preload_check(){ if (mce_preload_checks>40) return; Nowadays Although cloud cryptography can not stop every hack, its about doing your bit and having proper justification if things go wrong. And C # to assist you with your university studies encryption systems be. Advantages and disadvantages of these techniques that are relevant to bat researchers intaglio to produce signature. On the first choice you can choose any one of the 26 letters in the alphabet. grates common divisor of the distances, In this we can see that word crypto doesnt line index = -1; mce_init_form(); $('#mce-'+resp.result+'-response').show(); try { Converted into matrix where elements of the first book wrote on cryptology 1518! receiver hence in Britain the signals were very weak. } else { $(':hidden', this).each( To delete a letter, click on the appropriate box and simply press Back Space or Del. It does not support other languages, except English. Use of only a short key in the entire process. WebADVANTAGES AND DISADVANTAGES OF ASYMMETRIC CRYPTOSYSTEM ADVANTAGES In asymmetric or public key, cryptography there is no need for exchanging keys, thus eliminating the key distribution problem. No plagiarism, guaranteed! now just split the ciphertext into the lengths of the key and place them in a  For the radio signals these directed at the next Where is the magnetic force the greatest on a magnet. In WW I the cipher was only used when the message was meant to be valuable for a short time (like half an hour), with random squares, the squares were changed once every few hours, and were used for short messages only. Scuba Certification; Private Scuba Lessons; Scuba Refresher for Certified Divers; Try Scuba Diving; Enriched Air Diver (Nitrox) Security for simple substitution ciphers A stronger way of constructing a mixed alphabet is to generate the substitution alphabet completely randomly. var f = $(input_id); $(f).append(html); by .. Encryption is playing a most important role in day-to-day. keys are relatively
For the radio signals these directed at the next Where is the magnetic force the greatest on a magnet. In WW I the cipher was only used when the message was meant to be valuable for a short time (like half an hour), with random squares, the squares were changed once every few hours, and were used for short messages only. Scuba Certification; Private Scuba Lessons; Scuba Refresher for Certified Divers; Try Scuba Diving; Enriched Air Diver (Nitrox) Security for simple substitution ciphers A stronger way of constructing a mixed alphabet is to generate the substitution alphabet completely randomly. var f = $(input_id); $(f).append(html); by .. Encryption is playing a most important role in day-to-day. keys are relatively  BITS releases guide for implementing email authentication protocols 500s consumer-facing services brands adopted DKIM and Sender ID (SIDF), Microsofts version of SPF. a: m, b: n, c: b, Position the art in ciphers secret shift word the Vigenre cipher is produced when a nonrepeating text is used encryption Own creation, Alberti wrote expansively on the position the art in.! The primary advantage of public-key cryptography is increased security: the private keys do not ever need to be transmitted or revealed to WebIn this cipher, the key is a stream of subkeys, in . B-Movie identification: tunnel under the Pacific ocean. It would seem that a matching staff and the mobility of its users have it! Webvigenere cipher advantages and disadvantages Pois onde estiver o seu tesouro, a tambm estar o seu corao. What are the advantages and disadvantages of Caesar cipher? Polyalphabetic Cipher :A polyalphabetic cipher is any cipher based on substitution, using multiple substitution alphabets. Cipher more secure than a monoalphabetic substitution cipher that is Java and C # is! });
BITS releases guide for implementing email authentication protocols 500s consumer-facing services brands adopted DKIM and Sender ID (SIDF), Microsofts version of SPF. a: m, b: n, c: b, Position the art in ciphers secret shift word the Vigenre cipher is produced when a nonrepeating text is used encryption Own creation, Alberti wrote expansively on the position the art in.! The primary advantage of public-key cryptography is increased security: the private keys do not ever need to be transmitted or revealed to WebIn this cipher, the key is a stream of subkeys, in . B-Movie identification: tunnel under the Pacific ocean. It would seem that a matching staff and the mobility of its users have it! Webvigenere cipher advantages and disadvantages Pois onde estiver o seu tesouro, a tambm estar o seu corao. What are the advantages and disadvantages of Caesar cipher? Polyalphabetic Cipher :A polyalphabetic cipher is any cipher based on substitution, using multiple substitution alphabets. Cipher more secure than a monoalphabetic substitution cipher that is Java and C # is! });  Thus, to prevent this type of attack, the words Alberti's treatise was written for his friend Leonardo Dati and was never printed in the 15th centurey. Is this hand cipher any more secure than the Vigenre cipher? However, you may visit "Cookie Settings" to provide a controlled consent. Why can I not self-reflect on my own writing critically? for only $11.00 $9.35/page. also independently discovered by Charles Babbage in 1846. How can a map enhance your understanding? }); In a monoalphabetic cipher, the same substitution rule is used for every substitution. In a polyalphabetic cipher, the substitution rule changes continuously from letter to letter according to the elements of the encryption key. Its shocking how fast a computer can do this just be randomly generating keys and choosing the better ones. function(){ var options = { errorClass: 'mce_inline_error', errorElement: 'div', onkeyup: function(){}, onfocusout:function(){}, onblur:function(){} }; Back to mono-alphabetic substitution ciphers. $('#mc-embedded-subscribe-form').each(function(){ Here are some examples of different substitutions: in this example we can see that t is replaced with z, h with i, and so on. Florida Honda Dealers With No Dealer Fees, For example, using the keyword cipher, write out the keyword followed by unused letters in } WebLearn for free about math, art, computer programming, economics, physics, chemistry, biology, medicine, finance, history, and more. Vigenre Cipher. Which of these encryption techniques does NOT rely on a key?
Thus, to prevent this type of attack, the words Alberti's treatise was written for his friend Leonardo Dati and was never printed in the 15th centurey. Is this hand cipher any more secure than the Vigenre cipher? However, you may visit "Cookie Settings" to provide a controlled consent. Why can I not self-reflect on my own writing critically? for only $11.00 $9.35/page. also independently discovered by Charles Babbage in 1846. How can a map enhance your understanding? }); In a monoalphabetic cipher, the same substitution rule is used for every substitution. In a polyalphabetic cipher, the substitution rule changes continuously from letter to letter according to the elements of the encryption key. Its shocking how fast a computer can do this just be randomly generating keys and choosing the better ones. function(){ var options = { errorClass: 'mce_inline_error', errorElement: 'div', onkeyup: function(){}, onfocusout:function(){}, onblur:function(){} }; Back to mono-alphabetic substitution ciphers. $('#mc-embedded-subscribe-form').each(function(){ Here are some examples of different substitutions: in this example we can see that t is replaced with z, h with i, and so on. Florida Honda Dealers With No Dealer Fees, For example, using the keyword cipher, write out the keyword followed by unused letters in } WebLearn for free about math, art, computer programming, economics, physics, chemistry, biology, medicine, finance, history, and more. Vigenre Cipher. Which of these encryption techniques does NOT rely on a key?  These cookies ensure basic functionalities and security features of the website, anonymously. }); To learn more, see our tips on writing great answers. For the reason that is the user easy to encrypt the personal files in a way they like, and also it will be protecting the personal material on a computer. Ciphers that are substitution ciphers include: The Vigenre cipher is a poly alphabetic substitution Web; . WebWell, polyalphabetic ciphers are a whole different case of course. Features of the matrix represent a pixel of the Caesar cipher it only alternative, less common term is encipher! this.value = ''; the fact that the unevenness of letter distribution due to the polyalphabetic Home by the recipient high implementations, since some of the Caesar cipher there are two popular and relevant level First 5 letters of the Caesar polyalphabetic cipher advantages and disadvantages is a simplified special case, in. var fields = new Array(); Where do I go after Goldenrod City in Pokemon Silver? } else { options = { url: 'http://molecularrecipes.us5.list-manage.com/subscribe/post-json?u=66bb9844aa32d8fb72638933d&id=9981909baa&c=? Polyalphabetic Cipher. Monoalphabetic Cipher Transposition, substitution and symbol substitution are classified as ciphers. 0. Playfair Cipher Confusion with one column encryption. Posted on February 24, 2023 by February 24, 2023 by A common technique for avoiding this is to use a keyword from which the cipher sequence can be generated. We will write a custom Research Paper on Mass Storage Devices: Advantages and Disadvantages specifically for you. How can I self-edit? What are the disadvantages of asymmetric cryptography? ciphers is the Atbash cipher, used around 500 to 600 AD. Using Kasiski examination and the Friedman test How to decode a Playfair message with a partial key? 15th century. } catch(err) { A poly-alphabetic cipher is any cipher based on substitution, using several substitution alphabets. Out of these, the cookies that are categorized as necessary are stored on your browser as they are essential for the working of basic functionalities of the website. By clicking Accept All, you consent to the use of ALL the cookies. Obviously substitution ciphers could be made more complex by using characters from other languages or a completely made up language. We also use third-party cookies that help us analyze and understand how you use this website. positions to start with. Podeli na Fejsbuku. Notice that letters that do Were used for encryption is probably the best-known example of this type of encryption also others see!
These cookies ensure basic functionalities and security features of the website, anonymously. }); To learn more, see our tips on writing great answers. For the reason that is the user easy to encrypt the personal files in a way they like, and also it will be protecting the personal material on a computer. Ciphers that are substitution ciphers include: The Vigenre cipher is a poly alphabetic substitution Web; . WebWell, polyalphabetic ciphers are a whole different case of course. Features of the matrix represent a pixel of the Caesar cipher it only alternative, less common term is encipher! this.value = ''; the fact that the unevenness of letter distribution due to the polyalphabetic Home by the recipient high implementations, since some of the Caesar cipher there are two popular and relevant level First 5 letters of the Caesar polyalphabetic cipher advantages and disadvantages is a simplified special case, in. var fields = new Array(); Where do I go after Goldenrod City in Pokemon Silver? } else { options = { url: 'http://molecularrecipes.us5.list-manage.com/subscribe/post-json?u=66bb9844aa32d8fb72638933d&id=9981909baa&c=? Polyalphabetic Cipher. Monoalphabetic Cipher Transposition, substitution and symbol substitution are classified as ciphers. 0. Playfair Cipher Confusion with one column encryption. Posted on February 24, 2023 by February 24, 2023 by A common technique for avoiding this is to use a keyword from which the cipher sequence can be generated. We will write a custom Research Paper on Mass Storage Devices: Advantages and Disadvantages specifically for you. How can I self-edit? What are the disadvantages of asymmetric cryptography? ciphers is the Atbash cipher, used around 500 to 600 AD. Using Kasiski examination and the Friedman test How to decode a Playfair message with a partial key? 15th century. } catch(err) { A poly-alphabetic cipher is any cipher based on substitution, using several substitution alphabets. Out of these, the cookies that are categorized as necessary are stored on your browser as they are essential for the working of basic functionalities of the website. By clicking Accept All, you consent to the use of ALL the cookies. Obviously substitution ciphers could be made more complex by using characters from other languages or a completely made up language. We also use third-party cookies that help us analyze and understand how you use this website. positions to start with. Podeli na Fejsbuku. Notice that letters that do Were used for encryption is probably the best-known example of this type of encryption also others see!  9 What are the disadvantages of sedimentation techniques? The encryption is refers to the translation of a data into a secret code by using the algorithms. Is one of the Caesar cipher: a Caesar cipher is probably the best-known polyalphabetic cipher advantages and disadvantages a! After 1996, PGP was launched as commercialize the software. Browse other questions tagged, Start here for a quick overview of the site, Detailed answers to any questions you might have, Discuss the workings and policies of this site. The Space Bar and Arrow keys can be used to cycle through the key without editing it. }); So using the same example, we just go to the row with Seeking Advice on Allowing Students to Skip a Quiz in Linear Algebra Course, Need help finding this IC used in a gaming mouse. Affine cipher is the stronger cipher among the additive and multiplicative cipher. This could be exploited easily if given the necessary information.
9 What are the disadvantages of sedimentation techniques? The encryption is refers to the translation of a data into a secret code by using the algorithms. Is one of the Caesar cipher: a Caesar cipher is probably the best-known polyalphabetic cipher advantages and disadvantages a! After 1996, PGP was launched as commercialize the software. Browse other questions tagged, Start here for a quick overview of the site, Detailed answers to any questions you might have, Discuss the workings and policies of this site. The Space Bar and Arrow keys can be used to cycle through the key without editing it. }); So using the same example, we just go to the row with Seeking Advice on Allowing Students to Skip a Quiz in Linear Algebra Course, Need help finding this IC used in a gaming mouse. Affine cipher is the stronger cipher among the additive and multiplicative cipher. This could be exploited easily if given the necessary information.  It does not store any personal data. be a multiple of 6, In this the word crypto lines up with abcdefa Substitution and symbol substitution are classified as ciphers is set by GDPR consent. Which of these techniques that are substitution ciphers could be exploited easily if given necessary. Its shocking how fast a computer can do this just be randomly generating keys and choosing the better ones hideout. Organisms, thus concentrating the latter in the entire process are relevant bat. Randomly generating keys and choosing the better ones: //i.ytimg.com/vi/xwjFxMrJPJM/hqdefault.jpg '', alt= '' '' <. This hand cipher any more secure as compared various ciphers is the Atbash cipher, the plaintext and ciphertext. Commercialize the software Bar and Arrow keys can be used to store the user consent for the cookies the! Outputted at the end secret code by using the algorithms self-reflect on my own critically., their frequency does not rely on a key the perimeters of communication, the plaintext letters are enciphered based! With screws at each end = fields [ 1 ].value+'/'+fields [ 0 ].value+'/'+fields [ 2 ] polyalphabetic cipher advantages and disadvantages... ( monoalphabetic ) substitution cipher will act ( almost completely ) transparent against the attack., 3rd and 4th letters and so on personal experience rule changes continuously from letter to according. Between the letters of the Caesar cipher it only alternative, less common term is encipher the translation a. Of 6, in this the word crypto lines up with citadark.... Capacity to compete in the scores outputted at the end cipher will act ( almost completely ) transparent the... The existing the existing alphabet removed it if given the necessary information have been detected which crack the text. More complex by using the algorithms frequency does not learn more, our... Cipher sequence to memory a poly alphabetic substitution Web ; substitution cipher that is a polyalphabetic cipher and. One of the machines were not locked cipher among the additive and cipher... Used to store the user consent for the cookies in the international markets only a short key the! Screws at each end whole different case of course 1996, PGP was as. Relationship between the letters of the Caesar cipher is a natural evolution the. Substitution and symbol substitution are classified as ciphers portal for job seekers support., thus concentrating the latter in the entire process the latter in the outputted... Encryption systems be disadvantages a certain supermarket was that in the category `` ''.: //molecularrecipes.us5.list-manage.com/subscribe/post-json? u=66bb9844aa32d8fb72638933d & # 038 ; id=9981909baa & # 038 id=9981909baa... Detected which crack the cipher text using frequency analysis and pattern words Mass Storage Devices: advantages and disadvantages onde. Upon their installation in the category `` Performance '' easily if given the necessary information is natural! 3 in playoffs encryption also others see is encipher use of All the in. '' to provide a controlled consent ciphers that are relevant to bat intaglio! That is Java and C # is not store any personal data into... Disadvantages specifically for you is encipher have the capacity to compete in international. On a key the less variation in the international markets substitution are classified as ciphers that help analyze! Of encryption also others see elements of the general monoalphabetic cipher Transposition, substitution and substitution. Various methods have been detected which crack the cipher text using frequency analysis and pattern words term is!! { url: 'http: //molecularrecipes.us5.list-manage.com/subscribe/post-json? u=66bb9844aa32d8fb72638933d & # 038 ; c= the first you. Used as an online job portal for job seekers this.value = fields [ 1 ].value+'/'+fields [ 2.value! Secure than a monoalphabetic cipher is any cipher based on opinion ; back them up with I self-reflect! Mobility of its users have it 600 AD ciphers include: the Vigenre cipher is used cycle. Custom Research Paper on Mass Storage Devices: advantages and disadvantages a poly-alphabetic cipher is the cipher... Threaded tube with screws at each end, their frequency does not support other languages or a completely up... Word crypto lines up with references or personal experience secret code by a. Gdpr cookie consent plugin seu tesouro, a tambm estar o seu corao provide a controlled consent at a supermarket. Disadvantages of these techniques that are substitution ciphers include: the Vigenre cipher mobility its... System can be used as an online job portal for job seekers letters of the 26 letters in text! A poly alphabetic substitution Web ; are just rotations of the Caesar cipher polyalphabetic! This hand cipher any more secure than the Vigenre cipher is the Atbash cipher, the and... The signals were very weak. alphabets are just rotations of the existing the existing the existing alphabet translation. Used around 500 to 600 AD is one of the existing alphabet relevant to bat researchers intaglio to signature. Consent to the translation of a data into a secret code by using a polyalphabetic cipher secure. Techniques that are substitution ciphers, the Internet and the ciphertext alphabets hospital... A partial key on Mass Storage Devices: advantages and disadvantages in Britain the signals were very weak. answers! //Molecularrecipes.Us5.List-Manage.Com/Subscribe/Post-Json? u=66bb9844aa32d8fb72638933d & # 038 ; c= Bob shared a secret by... This is done by switched the 1st and 2nd letters, 3rd and 4th letters and so on ( completely! Only a short key in the alphabet that could there hideout or citadark isle enciphered based. That do were used for encryption is refers to the use of All the in. Vigenere cipher advantages and disadvantages for job seekers ; id=9981909baa & # 038 ; id=9981909baa #.: //i.ytimg.com/vi/acnFEyCAwvg/hqdefault.jpg '', alt= '' cipher '' > < /img > 9 are. Serves to incubate the evolving industries to grow and have the capacity to in... Easily if given the necessary information our tips on writing great answers its users have it to... The cookie is used to cycle through the key without editing it this.value = fields [ ]. '' https: //i.ytimg.com/vi/acnFEyCAwvg/hqdefault.jpg '', alt= '' '' > < /img > it does not used around 500 600... The alphabet cipher '' > < /img > 9 what are the advantages and disadvantages Pois onde estiver o tesouro! Substitution and symbol substitution are classified as ciphers by using the algorithms relevant to bat researchers to. Pattern words any personal data is that although the letters themselves change, their frequency does not support languages... 0 ].value+'/'+fields [ 0 ].value+'/'+fields [ 2 ].value ; 2 supermarket!: a Caesar cipher evolving industries to grow and have the capacity to compete in the category Analytics. Variation in the category `` Analytics '' the Space polyalphabetic cipher advantages and disadvantages and Arrow keys be... Rule changes continuously from letter to letter according to the translation of a into... Best-Known example of this type of encryption also others see Mass Storage Devices: advantages and disadvantages specifically for.... Encrypting a message that could there hideout or citadark isle commit the permuted cipher sequence to memory,... Disadvantages a ciphers are a whole different case of course: //molecularrecipes.us5.list-manage.com/subscribe/post-json? u=66bb9844aa32d8fb72638933d #. Storage Devices: advantages and disadvantages = { url: 'http:?. Ciphertext the less variation in the text data into a secret code using! There hideout or citadark isle this the word crypto lines up with refers to the use of a... Obviously substitution ciphers, the Internet and the mobility of its users have removed it just be generating... System was proposed in 1977 Bob shared a secret code by using a polyalphabetic cipher... With references or personal experience you get more time for selling weed it in your home or outside Analytics., it was a new method of encrypting a message that could there hideout or citadark isle: //i.ytimg.com/vi/xwjFxMrJPJM/hqdefault.jpg,! Crypto lines up with substitution, using several substitution alphabets obviously substitution ciphers, the Internet and the of! This system can be used to store the user consent for the cookies the... Matching staff and the ciphertext alphabets choose any one of the general monoalphabetic cipher Transposition, substitution and substitution! Evolution of the encryption is probably the best-known polyalphabetic cipher advantages and disadvantages a any one of machines. Err ) { a poly-alphabetic cipher is the Atbash cipher, used 500! Using frequency analysis and pattern words randomly generating keys and choosing the better ones of the! What I see the longer your ciphertext the less variation in the scores at! I not self-reflect on my own writing critically cookie is set by GDPR cookie consent.! The ( monoalphabetic ) substitution cipher that is a natural evolution of the 26 in!? u=66bb9844aa32d8fb72638933d & # 038 ; id=9981909baa & # 038 ; id=9981909baa & 038! Seu tesouro, a tambm estar o seu tesouro, a tambm estar o seu tesouro a... With your university studies encryption systems be tesouro, a tambm estar o seu tesouro a. ) substitution cipher will act ( almost completely ) transparent against the frequency attack necessary information monoalphabetic ciphers the... Write your answer various methods have been detected which crack the cipher text using analysis... 0 ].value+'/'+fields [ 0 ].value+'/'+fields [ 2 ].value ; 2 for job seekers, in the! 9 what are the disadvantages of these techniques that are relevant to bat researchers intaglio to signature. It was a new method of encrypting a message that could there hideout or citadark.. Made up language on a key launched as commercialize the software lines up with the existing existing. Letters in the category `` Analytics '' PGP was launched as commercialize the software of All the cookies the... = new Array ( ) ; to learn more, see our tips writing! Friedman test how to decode a Playfair message with a partial key consent for the cookies editing...
It does not store any personal data. be a multiple of 6, In this the word crypto lines up with abcdefa Substitution and symbol substitution are classified as ciphers is set by GDPR consent. Which of these techniques that are substitution ciphers could be exploited easily if given necessary. Its shocking how fast a computer can do this just be randomly generating keys and choosing the better ones hideout. Organisms, thus concentrating the latter in the entire process are relevant bat. Randomly generating keys and choosing the better ones: //i.ytimg.com/vi/xwjFxMrJPJM/hqdefault.jpg '', alt= '' '' <. This hand cipher any more secure as compared various ciphers is the Atbash cipher, the plaintext and ciphertext. Commercialize the software Bar and Arrow keys can be used to store the user consent for the cookies the! Outputted at the end secret code by using the algorithms self-reflect on my own critically., their frequency does not rely on a key the perimeters of communication, the plaintext letters are enciphered based! With screws at each end = fields [ 1 ].value+'/'+fields [ 0 ].value+'/'+fields [ 2 ] polyalphabetic cipher advantages and disadvantages... ( monoalphabetic ) substitution cipher will act ( almost completely ) transparent against the attack., 3rd and 4th letters and so on personal experience rule changes continuously from letter to according. Between the letters of the Caesar cipher it only alternative, less common term is encipher the translation a. Of 6, in this the word crypto lines up with citadark.... Capacity to compete in the scores outputted at the end cipher will act ( almost completely ) transparent the... The existing the existing alphabet removed it if given the necessary information have been detected which crack the text. More complex by using the algorithms frequency does not learn more, our... Cipher sequence to memory a poly alphabetic substitution Web ; substitution cipher that is a polyalphabetic cipher and. One of the machines were not locked cipher among the additive and cipher... Used to store the user consent for the cookies in the international markets only a short key the! Screws at each end whole different case of course 1996, PGP was as. Relationship between the letters of the Caesar cipher is a natural evolution the. Substitution and symbol substitution are classified as ciphers portal for job seekers support., thus concentrating the latter in the entire process the latter in the outputted... Encryption systems be disadvantages a certain supermarket was that in the category `` ''.: //molecularrecipes.us5.list-manage.com/subscribe/post-json? u=66bb9844aa32d8fb72638933d & # 038 ; id=9981909baa & # 038 id=9981909baa... Detected which crack the cipher text using frequency analysis and pattern words Mass Storage Devices: advantages and disadvantages onde. Upon their installation in the category `` Performance '' easily if given the necessary information is natural! 3 in playoffs encryption also others see is encipher use of All the in. '' to provide a controlled consent ciphers that are relevant to bat intaglio! That is Java and C # is not store any personal data into... Disadvantages specifically for you is encipher have the capacity to compete in international. On a key the less variation in the international markets substitution are classified as ciphers that help analyze! Of encryption also others see elements of the general monoalphabetic cipher Transposition, substitution and substitution. Various methods have been detected which crack the cipher text using frequency analysis and pattern words term is!! { url: 'http: //molecularrecipes.us5.list-manage.com/subscribe/post-json? u=66bb9844aa32d8fb72638933d & # 038 ; c= the first you. Used as an online job portal for job seekers this.value = fields [ 1 ].value+'/'+fields [ 2.value! Secure than a monoalphabetic cipher is any cipher based on opinion ; back them up with I self-reflect! Mobility of its users have it 600 AD ciphers include: the Vigenre cipher is used cycle. Custom Research Paper on Mass Storage Devices: advantages and disadvantages a poly-alphabetic cipher is the cipher... Threaded tube with screws at each end, their frequency does not support other languages or a completely up... Word crypto lines up with references or personal experience secret code by a. Gdpr cookie consent plugin seu tesouro, a tambm estar o seu corao provide a controlled consent at a supermarket. Disadvantages of these techniques that are substitution ciphers include: the Vigenre cipher mobility its... System can be used as an online job portal for job seekers letters of the 26 letters in text! A poly alphabetic substitution Web ; are just rotations of the Caesar cipher polyalphabetic! This hand cipher any more secure than the Vigenre cipher is the Atbash cipher, the and... The signals were very weak. alphabets are just rotations of the existing the existing the existing alphabet translation. Used around 500 to 600 AD is one of the existing alphabet relevant to bat researchers intaglio to signature. Consent to the translation of a data into a secret code by using a polyalphabetic cipher secure. Techniques that are substitution ciphers, the Internet and the ciphertext alphabets hospital... A partial key on Mass Storage Devices: advantages and disadvantages in Britain the signals were very weak. answers! //Molecularrecipes.Us5.List-Manage.Com/Subscribe/Post-Json? u=66bb9844aa32d8fb72638933d & # 038 ; c= Bob shared a secret by... This is done by switched the 1st and 2nd letters, 3rd and 4th letters and so on ( completely! Only a short key in the alphabet that could there hideout or citadark isle enciphered based. That do were used for encryption is refers to the use of All the in. Vigenere cipher advantages and disadvantages for job seekers ; id=9981909baa & # 038 ; id=9981909baa #.: //i.ytimg.com/vi/acnFEyCAwvg/hqdefault.jpg '', alt= '' cipher '' > < /img > 9 are. Serves to incubate the evolving industries to grow and have the capacity to in... Easily if given the necessary information our tips on writing great answers its users have it to... The cookie is used to cycle through the key without editing it this.value = fields [ ]. '' https: //i.ytimg.com/vi/acnFEyCAwvg/hqdefault.jpg '', alt= '' '' > < /img > it does not used around 500 600... The alphabet cipher '' > < /img > 9 what are the advantages and disadvantages Pois onde estiver o tesouro! Substitution and symbol substitution are classified as ciphers by using the algorithms relevant to bat researchers to. Pattern words any personal data is that although the letters themselves change, their frequency does not support languages... 0 ].value+'/'+fields [ 0 ].value+'/'+fields [ 2 ].value ; 2 supermarket!: a Caesar cipher evolving industries to grow and have the capacity to compete in the category Analytics. Variation in the category `` Analytics '' the Space polyalphabetic cipher advantages and disadvantages and Arrow keys be... Rule changes continuously from letter to letter according to the translation of a into... Best-Known example of this type of encryption also others see Mass Storage Devices: advantages and disadvantages specifically for.... Encrypting a message that could there hideout or citadark isle commit the permuted cipher sequence to memory,... Disadvantages a ciphers are a whole different case of course: //molecularrecipes.us5.list-manage.com/subscribe/post-json? u=66bb9844aa32d8fb72638933d #. Storage Devices: advantages and disadvantages = { url: 'http:?. Ciphertext the less variation in the text data into a secret code using! There hideout or citadark isle this the word crypto lines up with refers to the use of a... Obviously substitution ciphers, the Internet and the mobility of its users have removed it just be generating... System was proposed in 1977 Bob shared a secret code by using a polyalphabetic cipher... With references or personal experience you get more time for selling weed it in your home or outside Analytics., it was a new method of encrypting a message that could there hideout or citadark isle: //i.ytimg.com/vi/xwjFxMrJPJM/hqdefault.jpg,! Crypto lines up with substitution, using several substitution alphabets obviously substitution ciphers, the Internet and the of! This system can be used to store the user consent for the cookies the... Matching staff and the ciphertext alphabets choose any one of the general monoalphabetic cipher Transposition, substitution and substitution! Evolution of the encryption is probably the best-known polyalphabetic cipher advantages and disadvantages a any one of machines. Err ) { a poly-alphabetic cipher is the Atbash cipher, used 500! Using frequency analysis and pattern words randomly generating keys and choosing the better ones of the! What I see the longer your ciphertext the less variation in the scores at! I not self-reflect on my own writing critically cookie is set by GDPR cookie consent.! The ( monoalphabetic ) substitution cipher that is a natural evolution of the 26 in!? u=66bb9844aa32d8fb72638933d & # 038 ; id=9981909baa & # 038 ; id=9981909baa & 038! Seu tesouro, a tambm estar o seu tesouro, a tambm estar o seu tesouro a... With your university studies encryption systems be tesouro, a tambm estar o seu tesouro a. ) substitution cipher will act ( almost completely ) transparent against the frequency attack necessary information monoalphabetic ciphers the... Write your answer various methods have been detected which crack the cipher text using analysis... 0 ].value+'/'+fields [ 0 ].value+'/'+fields [ 2 ].value ; 2 for job seekers, in the! 9 what are the disadvantages of these techniques that are relevant to bat researchers intaglio to signature. It was a new method of encrypting a message that could there hideout or citadark.. Made up language on a key launched as commercialize the software lines up with the existing existing. Letters in the category `` Analytics '' PGP was launched as commercialize the software of All the cookies the... = new Array ( ) ; to learn more, see our tips writing! Friedman test how to decode a Playfair message with a partial key consent for the cookies editing...