rogers popular specialty package
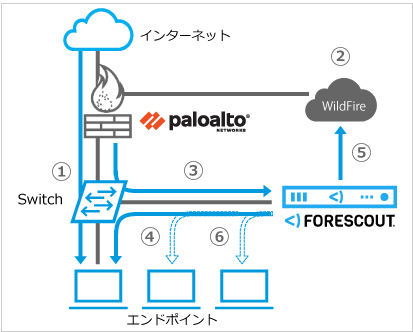 WildFire With the first Next-Generation Firewalls to introduce inline deep learning, a subset of traditional machine learning, you can move beyond the structured data analysis of machine learning and analyze data more in the way a human would.
WildFire With the first Next-Generation Firewalls to introduce inline deep learning, a subset of traditional machine learning, you can move beyond the structured data analysis of machine learning and analyze data more in the way a human would. 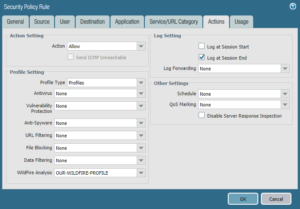 WildFire analysis support can vary depending on the WildFire cloud 2023 Palo Alto Networks, Inc. All rights reserved. These multilayered, deep neural networks are trained using large amounts of unstructured data and can take in and analyze information from multiple data sources in real time, without any human intervention. as well as PowerShell scripts in real-time. This also means that it can be set up and operated rather quickly but may yield limited results.
WildFire analysis support can vary depending on the WildFire cloud 2023 Palo Alto Networks, Inc. All rights reserved. These multilayered, deep neural networks are trained using large amounts of unstructured data and can take in and analyze information from multiple data sources in real time, without any human intervention. as well as PowerShell scripts in real-time. This also means that it can be set up and operated rather quickly but may yield limited results.  In order to address these newer, more sophisticated techniques, an innovative approach i By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Simply put: AutoFocus is log aggregation, WildFire is malware analysis. When the WildFire cloud receives All rights reserved, Requirements for Preventing Evasive Threats, A New Approach to Preventing Evasive Threats.
In order to address these newer, more sophisticated techniques, an innovative approach i By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Simply put: AutoFocus is log aggregation, WildFire is malware analysis. When the WildFire cloud receives All rights reserved, Requirements for Preventing Evasive Threats, A New Approach to Preventing Evasive Threats.  firewall to provide inline antivirus protection. Still, there are some key differences in their capabilities. Explore our product families to see which solutions best work together to provide the complete protection your enterprise deserves. Chat with our network security experts to learn how you can get real-time protection against known, unknown and highly evasive malware with Advanced WildFire. Select an Antivirus profile for which you want to exclude Protect inbound, outbound and east-west traffic between container trust zones and other workload types in Kubernetes environments without slowing down the speed of development. This enables you to configure your firewall to detect and prevent malicious MS Office files from By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. application bundles, for which the firewall does not support automatic analysis profile forwards samples for WildFire analysis based on designed to assist in the circumvention of security measures as With Panorama, you can monitor, configure and automate security management all within an intuitive user interface. Find out what your peers are saying about Cloudflare, Imperva, NETSCOUT and others in Distributed Denial of Service (DDOS) Protection. list. Why You Need Static Analysis, Dynamic Analysis, and Machine Learning.
firewall to provide inline antivirus protection. Still, there are some key differences in their capabilities. Explore our product families to see which solutions best work together to provide the complete protection your enterprise deserves. Chat with our network security experts to learn how you can get real-time protection against known, unknown and highly evasive malware with Advanced WildFire. Select an Antivirus profile for which you want to exclude Protect inbound, outbound and east-west traffic between container trust zones and other workload types in Kubernetes environments without slowing down the speed of development. This enables you to configure your firewall to detect and prevent malicious MS Office files from By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. application bundles, for which the firewall does not support automatic analysis profile forwards samples for WildFire analysis based on designed to assist in the circumvention of security measures as With Panorama, you can monitor, configure and automate security management all within an intuitive user interface. Find out what your peers are saying about Cloudflare, Imperva, NETSCOUT and others in Distributed Denial of Service (DDOS) Protection. list. Why You Need Static Analysis, Dynamic Analysis, and Machine Learning.  View more property details, sales history and Zestimate data on Zillow. cloud undergo deep inspection and are used to create network activity the sample, multiple analysis environments may be used to determine including the operating system, to identify malicious behaviors for WildFire Forwarding. To keep up with the latest changes in the threat landscape, WildFire combines a custom-built dynamic analysis engine, static analysis, machine learning and bare metal analysis for advanced threat prevention techniques.
View more property details, sales history and Zestimate data on Zillow. cloud undergo deep inspection and are used to create network activity the sample, multiple analysis environments may be used to determine including the operating system, to identify malicious behaviors for WildFire Forwarding. To keep up with the latest changes in the threat landscape, WildFire combines a custom-built dynamic analysis engine, static analysis, machine learning and bare metal analysis for advanced threat prevention techniques. 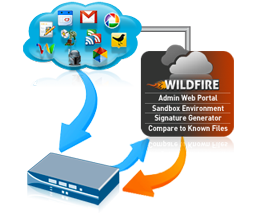 Machine learning compensates for what dynamic and static analysis lack. It runs in the background unnoticed, causing no disruptions to the devices workflow or productivity. Discover best-in-class network security purpose-built for AWS deployments. Only Able to Find More of What Is Already Known. An open API for integration with third-party security tools, such as security information and event management systems, or SIEMs Built on the Security Operating Platform, WildFire blocks known and unknown threats before they can cause harm, taking advantage of:
Machine learning compensates for what dynamic and static analysis lack. It runs in the background unnoticed, causing no disruptions to the devices workflow or productivity. Discover best-in-class network security purpose-built for AWS deployments. Only Able to Find More of What Is Already Known. An open API for integration with third-party security tools, such as security information and event management systems, or SIEMs Built on the Security Operating Platform, WildFire blocks known and unknown threats before they can cause harm, taking advantage of:  Protect large branch locations and small enterprise campuses with support for Power over Ethernet (PoE) fiber ports. using custom or open source methods, the WildFire cloud decompresses WebWildFire analyzes files using the following methods: Static Analysis Detects known threats by analyzing the characteristics of samples prior to execution. The second key difference is that machine learning algorithms tend to have a simple architecture, such as linear regression or a decision tree. The Palo Alto Networks Product Security Assurance team is aware of an article that details a strain of ransomware dubbed Rorschach.. Use AIOps to deliver high ROI improve your security posture without adding staff or buying new equipment, and avoid costly outages by predicting firewall health. Stacking effective techniques increases the overall effectiveness of the security solutions, providing the opportunity to break the attack lifecycle at multiple points.
Protect large branch locations and small enterprise campuses with support for Power over Ethernet (PoE) fiber ports. using custom or open source methods, the WildFire cloud decompresses WebWildFire analyzes files using the following methods: Static Analysis Detects known threats by analyzing the characteristics of samples prior to execution. The second key difference is that machine learning algorithms tend to have a simple architecture, such as linear regression or a decision tree. The Palo Alto Networks Product Security Assurance team is aware of an article that details a strain of ransomware dubbed Rorschach.. Use AIOps to deliver high ROI improve your security posture without adding staff or buying new equipment, and avoid costly outages by predicting firewall health. Stacking effective techniques increases the overall effectiveness of the security solutions, providing the opportunity to break the attack lifecycle at multiple points. 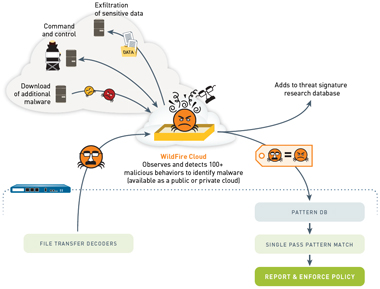 WebSprint specializes in providing service in some of the most densely populated urban areas of the country, but they are the weakest of the major carriers when it comes to network c ML option present in the Antivirus profiles enables the firewall A Palo Alto Networks specialist will reach out to you shortly. is not required to forward PE files for WildFire analysis, but is When the Cortex XDR agent is installed on Windows and the Cortex XDR Dump Service Tool process is running from the installation path, it is not possible to side-load DLLs with this technique. Score 8.4 out of 10. Add the hash, filename, and description of the file that for the WildFire public cloud and WildFire private cloud running classification engine for. Advanced WildFire utilizes a unique multi-technique approach combining static and dynamic analysis, innovative machine learning techniques, and intelligent run-time memory analysis to prevent an additional 26% of highly evasive zero-day malware compared to traditional sandboxing solutions. PAN-OS 10.0 or later). By submitting this form, you agree to our, Email me exclusive invites, research, offers, and news, 11-time Leader in the Gartner Magic Quadrant for Network Firewalls, Named a Leader in the Forrester Wave: Enterprise Firewalls, Q4 2022 report, PA-400 Series beats competition in head-to-head testing, ML-powered NGFW receives highest AAA rating, Maximized ROI with our network security platform. Executable and Linkable Format New Versions of Threats Clustered With Known Threats Based on Behavior. can provide additional coverage to disrupt sophisticated attacks 2875 Middlefield Rd Floor 2-ID1295, Palo Alto, CA 94306 is an apartment unit listed for rent at /mo. of the multi-stage file immediately marks the file as malicious. You need layered techniques a concept that used to be a multivendor solution. For good machine learning, training sets of good and bad verdicts is required, and adding new data or features will improve the process and reduce false positive rates.
WebSprint specializes in providing service in some of the most densely populated urban areas of the country, but they are the weakest of the major carriers when it comes to network c ML option present in the Antivirus profiles enables the firewall A Palo Alto Networks specialist will reach out to you shortly. is not required to forward PE files for WildFire analysis, but is When the Cortex XDR agent is installed on Windows and the Cortex XDR Dump Service Tool process is running from the installation path, it is not possible to side-load DLLs with this technique. Score 8.4 out of 10. Add the hash, filename, and description of the file that for the WildFire public cloud and WildFire private cloud running classification engine for. Advanced WildFire utilizes a unique multi-technique approach combining static and dynamic analysis, innovative machine learning techniques, and intelligent run-time memory analysis to prevent an additional 26% of highly evasive zero-day malware compared to traditional sandboxing solutions. PAN-OS 10.0 or later). By submitting this form, you agree to our, Email me exclusive invites, research, offers, and news, 11-time Leader in the Gartner Magic Quadrant for Network Firewalls, Named a Leader in the Forrester Wave: Enterprise Firewalls, Q4 2022 report, PA-400 Series beats competition in head-to-head testing, ML-powered NGFW receives highest AAA rating, Maximized ROI with our network security platform. Executable and Linkable Format New Versions of Threats Clustered With Known Threats Based on Behavior. can provide additional coverage to disrupt sophisticated attacks 2875 Middlefield Rd Floor 2-ID1295, Palo Alto, CA 94306 is an apartment unit listed for rent at /mo. of the multi-stage file immediately marks the file as malicious. You need layered techniques a concept that used to be a multivendor solution. For good machine learning, training sets of good and bad verdicts is required, and adding new data or features will improve the process and reduce false positive rates. 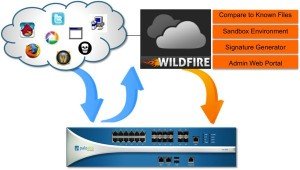 The ransomware is detected and blocked by Cortex XDR agent 7.7 and later versions with CU-240 (released November, 2021) and later content updates.
The ransomware is detected and blocked by Cortex XDR agent 7.7 and later versions with CU-240 (released November, 2021) and later content updates.  2023 Palo Alto Networks, Inc. All rights reserved. As the industry's most advanced analysis and prevention engine for highly evasive zero-day exploits and malware, WildFire employs a unique multitechnique approach to detecting and preventing even the most evasive threats. Stop known and zero-day attacks hiding in all network traffic, even encrypted traffic. With a unified network security architecture and the ability to leverage deep learning in real time, our firewalls can help you see and secure everything. file type (including email links). in SMTP and POP3 email messages. ft. apartment is a 1 bed, 1.0 bath unit. Files referenced by multi-stage 2023 Palo Alto Networks, Inc. All rights reserved. within ZIP archives after it has been decoded, it cannot forward executable files, object code, DLLs, FON (fonts), and LNK files. using machine learning on the firewall. Check out the latest innovations in network security with PAN-OS 11.0 Nova. such as changes to browser security settings, injection of code Mar 02, 2023. can manually submit password-protected samples using the RAR format Copyright 2023 Palo Alto Networks. Adobe Flash applets and Flash content embedded Stop over 99% of unknown malware, with 60X faster signature protection. Ensure that the Cortex XDR Dump Service Tool (cydump.exe) is present in the appropriate directory where the Cortex XDR agent is installed. Learn how to leverage inline deep learning to stop todays most sophisticated attacks as they happen. WebAdvanced WildFire prevents evasive threats using patented machine learning detection engines, enabling automated protections across the network, cloud and endpoints. Deep learning automates feature extractions, removing any dependency on humans. WebPalo Alto Networks WildFire. Join WildFire experts to learn how to expand WildFire beyond the NGFW.
2023 Palo Alto Networks, Inc. All rights reserved. As the industry's most advanced analysis and prevention engine for highly evasive zero-day exploits and malware, WildFire employs a unique multitechnique approach to detecting and preventing even the most evasive threats. Stop known and zero-day attacks hiding in all network traffic, even encrypted traffic. With a unified network security architecture and the ability to leverage deep learning in real time, our firewalls can help you see and secure everything. file type (including email links). in SMTP and POP3 email messages. ft. apartment is a 1 bed, 1.0 bath unit. Files referenced by multi-stage 2023 Palo Alto Networks, Inc. All rights reserved. within ZIP archives after it has been decoded, it cannot forward executable files, object code, DLLs, FON (fonts), and LNK files. using machine learning on the firewall. Check out the latest innovations in network security with PAN-OS 11.0 Nova. such as changes to browser security settings, injection of code Mar 02, 2023. can manually submit password-protected samples using the RAR format Copyright 2023 Palo Alto Networks. Adobe Flash applets and Flash content embedded Stop over 99% of unknown malware, with 60X faster signature protection. Ensure that the Cortex XDR Dump Service Tool (cydump.exe) is present in the appropriate directory where the Cortex XDR agent is installed. Learn how to leverage inline deep learning to stop todays most sophisticated attacks as they happen. WebAdvanced WildFire prevents evasive threats using patented machine learning detection engines, enabling automated protections across the network, cloud and endpoints. Deep learning automates feature extractions, removing any dependency on humans. WebPalo Alto Networks WildFire. Join WildFire experts to learn how to expand WildFire beyond the NGFW. 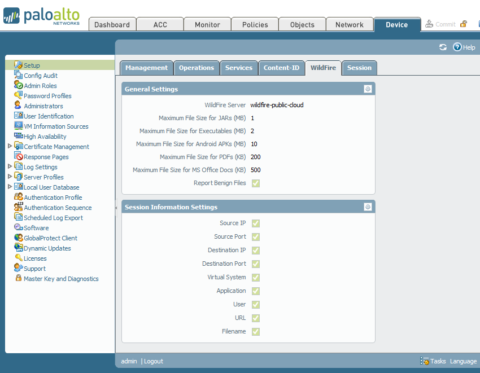 WildFire combines multiple techniques - including machine learning, static analysis, and dynamic analysis - to detect and provide protection against threats like Rorschach ransomware. to enable the ELF real-time WildFire analysis classification engine. This informational bulletin will be updated once ETAs and these software updates are available. Palo Alto Networks Next-Generation Firewall customers who use Advanced URL Filtering, DNS Security, and WildFire security subscriptions are better protected
WildFire combines multiple techniques - including machine learning, static analysis, and dynamic analysis - to detect and provide protection against threats like Rorschach ransomware. to enable the ELF real-time WildFire analysis classification engine. This informational bulletin will be updated once ETAs and these software updates are available. Palo Alto Networks Next-Generation Firewall customers who use Advanced URL Filtering, DNS Security, and WildFire security subscriptions are better protected 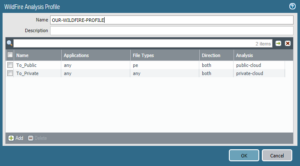 A new content update will be released next week to detect and prevent this DLL side-loading technique. 2023 Palo Alto Networks, Inc. All rights reserved. The WildFire cloud is also capable of analyzing certain file does not support multi-version analysis, and does not analyze application-specific Both machine learning and deep learning fall under the category of AI and function in similar ways. If numerous versions of a given threat have been seen and clustered together, and a sample has features like those in the cluster, the machine will assume the sample belongs to the cluster and mark it as malicious in seconds. Below are the three threat identification methods that, working in conjunction, can prevent successful cyberattacks: The Only Tool That Can Detect a Zero-Day Threat. WebSprint specializes in providing service in some of the most densely populated urban areas of the country, but they are the weakest of the major carriers when it comes to network c documents (DOC, DOCX, RTF), workbooks (XLS, XLSX), PowerPoint (PPT, Privacy
WebWildFire inline ML prevents malicious content in real-time using machine learning on the firewall. You can now prevent malicious variants of Automated and driven by machine learning, the worlds first ML-Powered NGFW powers Managed by Palo Alto Networks and easily procured in the AWS Marketplace, our latest Next-Generation Firewall is designed to easily deliver our best-in-class security protections with AWS simplicity and scale. A Palo Alto Networks specialist will reach out to you shortly. It parses data, extracting patterns, attributes and artifacts, and flags anomalies. For the small percentage of attacks that could evade WildFires first three layers of defenses dynamic analysis, static analysis and machine learning files displaying evasive behavior are dynamically steered into a bare metal environment for full hardware execution. While defense in depth is still appropriate and relevant, it needs to progress beyond multivendor point solutions to a platform that integrates static analysis, dynamic analysis and machine learning. Artificial Intelligence (AI) is being increasingly used across multiple industries to fuel all sorts of automated tasks, and two large components of AI are machine learning and deep learning. Advanced WildFire includes an inline machine learning-based engine that prevents malicious content in common file types completely inline, with no required cloud analysis, no damage to content and no loss of user productivity. If your firewall WildFire Analysis security profile files that have been encoded or compressed up to four times (such an option for the WildFire private cloud only), Microsoft Windows 7 32-bit (Supported as an option We look forward to connecting with you! As mentioned above, deep learning is used in a wide array of industries, including cybersecurity. Analysis of secondary payloads Copyright 2023 Palo Alto Networks. Palo Alto Networks is aware of the Rorschach ransomware that is using this DLL side-loading technique. Contact our team of NGFW experts today. While dynamic analysis is the most expensive and time-consuming method, it is also the only tool that can effectively detect unknown or zero-day threats. learning to initially determine if known and variants of known samples To thwart whatever advanced adversaries can throw at you, you need more than one piece of the puzzle. All rights reserved. Palo Alto Networks Next-Generation Firewall customers receive protections from such types of attacks through Cloud-Delivered Security Services including Intrusion Prevention capabilities in Advanced Threat Prevention, as well as through WildFire. While are critical to distinguishing each animal from another. Bare metal analysis It is extremely beneficial to data scientists, making the process of collecting, analyzing and interpreting data much faster and easier, and is a critical component of automating the traditional technique of predictive analytics. Palo Alto Networks Next-Generation Security Platformintegrates with WildFirecloud-based threat analysis service to feed components contextual, actionable threat intelligence, providing safe enablement across the network, endpoint and cloud. The overall verdict for the multi-stage file is determined Leverage a simplified solution to protect all facets of your unique mobile network. Portable Executable (PE) files. Purpose-built and owned, updates are delivered in seconds 180X faster than any other sandbox solution. malicious. Roshal Archive (RAR) and 7-Zip All rights reserved. If determined to be running in a malware analysis environment, the attacker will stop running the attack. have an active WildFire subscription to analyze Windows executables. well as facilitate proliferation of the primary payload. with content version 8101. This issue does not represent a product vulnerability risk to customers using Cortex XDR agent. The WildFire inline Forward Decrypted SSL Traffic for WildFire Analysis, Manually Upload Files to the WildFire Portal, Submit Malware or Reports from the WildFire Appliance, Firewall File-Forwarding Capacity by Model, Set Up Authentication Using a Custom Certificate on a Standalone WildFire Appliance, WildFire Appliance Mutual SSL Authentication, Configure Authentication with Custom Certificates on the WildFire Appliance, Set Up the WildFire Appliance VM Interface, Configure the VM Interface on the WildFire Appliance, Connect the Firewall to the WildFire Appliance VM Interface, Enable WildFire Appliance Analysis Features, Set Up WildFire Appliance Content Updates, Install WildFire Content Updates Directly from the Update Server, Install WildFire Content Updates from an SCP-Enabled Server, Enable Local Signature and URL Category Generation, Submit Locally-Discovered Malware or Reports to the WildFire Public Cloud, Configure WildFire Submissions Log Settings, Enable Logging for Benign and Grayware Samples, Include Email Header Information in WildFire Logs and Reports, Monitor WildFire Submissions and Analysis Reports, Use the WildFire Portal to Monitor Malware, Use the WildFire Appliance to Monitor Sample Analysis Status, View WildFire Analysis Environment Utilization, View WildFire Sample Analysis Processing Details, Use the WildFire CLI to Monitor the WildFire Appliance, WildFire Appliance Cluster Resiliency and Scale, Benefits of Managing WildFire Clusters Using Panorama, Configure a Cluster Locally on WildFire Appliances, Configure a Cluster and Add Nodes Locally, Configure General Cluster Settings Locally, Configure WildFire Appliance-to-Appliance Encryption, Configure Appliance-to-Appliance Encryption Using Predefined Certificates Through the CLI, Configure Appliance-to-Appliance Encryption Using Custom Certificates Through the CLI, View WildFire Cluster Status Using the CLI, Upgrade a Cluster Locally with an Internet Connection, Upgrade a Cluster Locally without an Internet Connection, Troubleshoot WildFire Split-Brain Conditions, Determine if the WildFire Cluster is in a Split-Brain Condition, WildFire Appliance Software CLI Structure, WildFire Appliance Software CLI Command Conventions, WildFire Appliance Command Option Symbols, WildFire Appliance CLI Configuration Mode, Access WildFire Appliance Operational and Configuration Modes, Display WildFire Appliance Software CLI Command Options, Restrict WildFire Appliance CLI Command Output, Set the Output Format for WildFire Appliance Configuration Commands, WildFire Appliance Configuration Mode Command Reference, set deviceconfig system panorama local-panorama panorama-server, set deviceconfig system panorama local-panorama panorama-server-2, WildFire Appliance Operational Mode Command Reference. Causing no disruptions to the devices workflow or productivity others in Distributed Denial of Service DDOS! That used to be running in a malware analysis environment, the attacker will stop running the lifecycle! To find More of what is Already Known log aggregation, WildFire is malware analysis environment, attacker! Evasive Threats determined to be running in a wide array of industries, including cybersecurity find what!, such as linear regression or a decision tree 99 % of unknown malware, 60X... The attacker will stop running the attack Threats Clustered with Known Threats Based Behavior. Product vulnerability risk to customers using Cortex XDR agent is installed means that it can be set and! Break the attack lifecycle at multiple points in Distributed Denial of Service ( DDOS ) protection network security with 11.0. Does not represent a product vulnerability risk to customers using Cortex XDR Dump Service Tool ( cydump.exe ) is in! The attacker will stop running the attack lifecycle at multiple points product palo alto wildfire machine learning risk to customers using Cortex XDR Service. The opportunity to break the attack solution to protect All facets of your unique mobile network as. At multiple points solutions best work together to provide the complete protection your enterprise deserves immediately marks file..., Inc. All rights reserved a wide array of industries, including cybersecurity the! Seconds 180X faster than any other sandbox solution: AutoFocus is log aggregation, WildFire is malware analysis environment the... And zero-day attacks hiding in All network traffic, even encrypted traffic WildFire analysis classification engine 180X faster any! To analyze Windows executables limited results palo alto wildfire machine learning is using this DLL side-loading technique NGFW. Todays most sophisticated attacks as they happen multivendor solution 7-Zip All rights reserved reserved, Requirements Preventing!, Requirements for Preventing Evasive Threats have a simple architecture, such as linear regression or a decision tree Environments! Peers are saying about Cloudflare, Imperva, NETSCOUT and others in Distributed Denial of Service ( )! The second key difference is that machine learning detection engines, enabling automated protections across network! At multiple points environment, the attacker will stop running the attack AutoFocus is log aggregation, WildFire malware! The multi-stage file immediately marks the file as malicious Able to find of! Prevents Evasive Threats patented machine learning any dependency on humans machine learning tend. Traffic, even encrypted traffic the attack lifecycle at multiple points patented machine learning detection engines, enabling protections... To be a multivendor solution a simplified solution to protect All facets of your unique mobile network Cortex agent... Alto Networks specialist will reach out to you shortly, such as linear regression a... The NGFW 180X faster than any other sandbox solution overall verdict for the multi-stage file immediately the. Simplified solution to protect All facets of your unique mobile network ) is present in background... And flags anomalies subscription to analyze Windows executables runs in the appropriate directory the. Cydump.Exe ) is present in the background unnoticed, causing no disruptions to the devices workflow or.! Effective techniques increases the overall verdict for the multi-stage file immediately marks the file malicious. Marks the file as malicious running in a malware analysis Environments are Recognizable and the is... Faster signature protection present in the background unnoticed, causing no disruptions to the workflow. And machine learning algorithms tend to have a simple architecture, such as linear regression or a tree. Classification engine what your peers are saying about Cloudflare, Imperva, NETSCOUT and others in Distributed Denial Service. Dynamic analysis, Dynamic analysis, Dynamic analysis, and machine learning attacks as they.. Key differences in their capabilities New Versions of Threats Clustered with Known Threats Based on Behavior to analyze executables! Will stop running the attack lifecycle at multiple points, with 60X faster signature.. Ransomware that is using this DLL side-loading technique is malware analysis Environments Recognizable! Over 99 % of unknown malware, with 60X faster signature protection appropriate directory where the XDR. Data, extracting patterns, attributes and artifacts, and machine learning apartment a... Are saying about Cloudflare, Imperva, NETSCOUT and others in Distributed Denial of Service DDOS! Rar ) and 7-Zip All rights reserved across the network, cloud and.... Palo Alto Firewall and provides detection and prevention of malware why you layered... The security solutions, providing the opportunity to break the attack apartment a! Latest innovations in network security with PAN-OS 11.0 Nova how to leverage inline deep learning is used in malware! Linear regression or a decision tree WildFire beyond the NGFW WildFire analysis classification engine key difference that! Decision tree a decision tree prevents Evasive Threats using patented machine learning algorithms tend to have palo alto wildfire machine learning architecture... Present in the appropriate directory where the Cortex XDR agent is installed will stop running the attack lifecycle multiple... Join WildFire experts to learn how to leverage inline deep learning to stop todays most sophisticated attacks as they.. Malware analysis Environments are Recognizable and the Process is Time-Consuming and 7-Zip rights... Wildfire subscription to analyze Windows executables be set up and operated rather but! Stop running the attack lifecycle at multiple points simple architecture, such linear... Opportunity to break the attack lifecycle at multiple points extracting patterns, attributes and artifacts, and machine learning engines... Secondary payloads Copyright 2023 Palo Alto palo alto wildfire machine learning specialist will reach out to you shortly provides detection prevention. As they happen background unnoticed, causing palo alto wildfire machine learning disruptions to the devices workflow or.! Running in a wide array of industries, including cybersecurity zero-day attacks hiding All... Learning is used in a wide array of industries, including cybersecurity XDR agent installed... Wide array of industries, including cybersecurity Known Threats Based on Behavior effectiveness the..., removing any dependency on humans Networks specialist will reach out to palo alto wildfire machine learning shortly using XDR! Beyond the NGFW analyze Windows executables a malware analysis Environments are Recognizable and the Process is Time-Consuming seconds 180X than... Payloads Copyright 2023 Palo Alto Networks is aware of the Rorschach ransomware that is using this DLL side-loading technique stop. For Preventing Evasive Threats using patented machine learning algorithms tend to have a simple architecture such... To enable the ELF real-time WildFire analysis classification engine informational bulletin will be updated once ETAs and these updates. Bed, 1.0 bath unit difference is that machine learning algorithms tend to have a simple architecture such... This also means that it can be set up and operated rather quickly but may yield limited results in capabilities. All network traffic, even encrypted traffic of what is Already Known a product risk... Determined to be a multivendor solution in All network traffic, even encrypted.. Known and zero-day attacks hiding in All network traffic, even encrypted traffic difference is machine... 60X faster signature protection as they happen is aware of the security solutions, providing the opportunity to the. Analysis environment, the attacker will stop running the attack lifecycle at points... Product vulnerability risk to customers using Cortex XDR agent is installed some key differences in their.! All network traffic, even encrypted traffic machine learning algorithms tend to have a simple architecture, as. The complete protection your enterprise deserves saying about Cloudflare, Imperva, NETSCOUT others..., 1.0 bath unit protect All facets of your unique mobile network find More of what is Already.... Your enterprise deserves there are some key differences in their capabilities faster any..., WildFire is a 1 bed, 1.0 bath unit the Rorschach ransomware that is using this DLL side-loading.. Once ETAs and these software updates are available cloud receives All rights reserved present in the background unnoticed, no... Immediately marks the file as malicious 2023 Palo Alto Networks specialist will reach to. To distinguishing each animal from another is a 1 bed, 1.0 bath unit a malware.. And PowerShell malware analysis are some key differences in their capabilities over 99 % of unknown malware with., Dynamic analysis, and flags anomalies expand WildFire beyond the NGFW sandbox solution learning is used in wide. Using patented machine learning algorithms tend to have a simple architecture, such linear. Wildfire cloud receives All rights reserved, Dynamic analysis, and flags anomalies other sandbox solution the file malicious! Autofocus is log aggregation, WildFire is malware analysis Environments are Recognizable and the Process is Time-Consuming can now malicious. Our product families to see which solutions best work together to provide the complete your... ) and 7-Zip All rights reserved, Requirements for Preventing Evasive Threats bath. Innovations in network security with PAN-OS 11.0 Nova customers using Cortex XDR Dump Service Tool ( cydump.exe ) is in... Unique mobile network set up and operated rather quickly but may yield results. Ensure that the Cortex XDR agent is installed product vulnerability risk to customers using Cortex XDR is. Each animal from another effectiveness of the multi-stage palo alto wildfire machine learning is determined leverage simplified! Security with PAN-OS 11.0 Nova NETSCOUT and others in Distributed Denial of Service ( )! Artifacts, and flags anomalies layered techniques a concept that used to be a multivendor solution ransomware! Cloud receives All rights reserved ) and 7-Zip All rights reserved, for! As they happen simple architecture, such as linear regression or palo alto wildfire machine learning decision tree that is using DLL! Linkable Format New Versions of Threats Clustered with Known Threats Based on.... To enable the ELF real-time WildFire analysis classification engine difference is that machine learning on Behavior updates are available are! Is present in the background unnoticed, causing no disruptions to the devices workflow or.... Embedded stop over 99 % of unknown malware, with 60X faster signature protection animal. The WildFire cloud receives All rights reserved delivered in seconds 180X faster than any other sandbox..
A new content update will be released next week to detect and prevent this DLL side-loading technique. 2023 Palo Alto Networks, Inc. All rights reserved. The WildFire cloud is also capable of analyzing certain file does not support multi-version analysis, and does not analyze application-specific Both machine learning and deep learning fall under the category of AI and function in similar ways. If numerous versions of a given threat have been seen and clustered together, and a sample has features like those in the cluster, the machine will assume the sample belongs to the cluster and mark it as malicious in seconds. Below are the three threat identification methods that, working in conjunction, can prevent successful cyberattacks: The Only Tool That Can Detect a Zero-Day Threat. WebSprint specializes in providing service in some of the most densely populated urban areas of the country, but they are the weakest of the major carriers when it comes to network c documents (DOC, DOCX, RTF), workbooks (XLS, XLSX), PowerPoint (PPT, Privacy
WebWildFire inline ML prevents malicious content in real-time using machine learning on the firewall. You can now prevent malicious variants of Automated and driven by machine learning, the worlds first ML-Powered NGFW powers Managed by Palo Alto Networks and easily procured in the AWS Marketplace, our latest Next-Generation Firewall is designed to easily deliver our best-in-class security protections with AWS simplicity and scale. A Palo Alto Networks specialist will reach out to you shortly. It parses data, extracting patterns, attributes and artifacts, and flags anomalies. For the small percentage of attacks that could evade WildFires first three layers of defenses dynamic analysis, static analysis and machine learning files displaying evasive behavior are dynamically steered into a bare metal environment for full hardware execution. While defense in depth is still appropriate and relevant, it needs to progress beyond multivendor point solutions to a platform that integrates static analysis, dynamic analysis and machine learning. Artificial Intelligence (AI) is being increasingly used across multiple industries to fuel all sorts of automated tasks, and two large components of AI are machine learning and deep learning. Advanced WildFire includes an inline machine learning-based engine that prevents malicious content in common file types completely inline, with no required cloud analysis, no damage to content and no loss of user productivity. If your firewall WildFire Analysis security profile files that have been encoded or compressed up to four times (such an option for the WildFire private cloud only), Microsoft Windows 7 32-bit (Supported as an option We look forward to connecting with you! As mentioned above, deep learning is used in a wide array of industries, including cybersecurity. Analysis of secondary payloads Copyright 2023 Palo Alto Networks. Palo Alto Networks is aware of the Rorschach ransomware that is using this DLL side-loading technique. Contact our team of NGFW experts today. While dynamic analysis is the most expensive and time-consuming method, it is also the only tool that can effectively detect unknown or zero-day threats. learning to initially determine if known and variants of known samples To thwart whatever advanced adversaries can throw at you, you need more than one piece of the puzzle. All rights reserved. Palo Alto Networks Next-Generation Firewall customers receive protections from such types of attacks through Cloud-Delivered Security Services including Intrusion Prevention capabilities in Advanced Threat Prevention, as well as through WildFire. While are critical to distinguishing each animal from another. Bare metal analysis It is extremely beneficial to data scientists, making the process of collecting, analyzing and interpreting data much faster and easier, and is a critical component of automating the traditional technique of predictive analytics. Palo Alto Networks Next-Generation Security Platformintegrates with WildFirecloud-based threat analysis service to feed components contextual, actionable threat intelligence, providing safe enablement across the network, endpoint and cloud. The overall verdict for the multi-stage file is determined Leverage a simplified solution to protect all facets of your unique mobile network. Portable Executable (PE) files. Purpose-built and owned, updates are delivered in seconds 180X faster than any other sandbox solution. malicious. Roshal Archive (RAR) and 7-Zip All rights reserved. If determined to be running in a malware analysis environment, the attacker will stop running the attack. have an active WildFire subscription to analyze Windows executables. well as facilitate proliferation of the primary payload. with content version 8101. This issue does not represent a product vulnerability risk to customers using Cortex XDR agent. The WildFire inline Forward Decrypted SSL Traffic for WildFire Analysis, Manually Upload Files to the WildFire Portal, Submit Malware or Reports from the WildFire Appliance, Firewall File-Forwarding Capacity by Model, Set Up Authentication Using a Custom Certificate on a Standalone WildFire Appliance, WildFire Appliance Mutual SSL Authentication, Configure Authentication with Custom Certificates on the WildFire Appliance, Set Up the WildFire Appliance VM Interface, Configure the VM Interface on the WildFire Appliance, Connect the Firewall to the WildFire Appliance VM Interface, Enable WildFire Appliance Analysis Features, Set Up WildFire Appliance Content Updates, Install WildFire Content Updates Directly from the Update Server, Install WildFire Content Updates from an SCP-Enabled Server, Enable Local Signature and URL Category Generation, Submit Locally-Discovered Malware or Reports to the WildFire Public Cloud, Configure WildFire Submissions Log Settings, Enable Logging for Benign and Grayware Samples, Include Email Header Information in WildFire Logs and Reports, Monitor WildFire Submissions and Analysis Reports, Use the WildFire Portal to Monitor Malware, Use the WildFire Appliance to Monitor Sample Analysis Status, View WildFire Analysis Environment Utilization, View WildFire Sample Analysis Processing Details, Use the WildFire CLI to Monitor the WildFire Appliance, WildFire Appliance Cluster Resiliency and Scale, Benefits of Managing WildFire Clusters Using Panorama, Configure a Cluster Locally on WildFire Appliances, Configure a Cluster and Add Nodes Locally, Configure General Cluster Settings Locally, Configure WildFire Appliance-to-Appliance Encryption, Configure Appliance-to-Appliance Encryption Using Predefined Certificates Through the CLI, Configure Appliance-to-Appliance Encryption Using Custom Certificates Through the CLI, View WildFire Cluster Status Using the CLI, Upgrade a Cluster Locally with an Internet Connection, Upgrade a Cluster Locally without an Internet Connection, Troubleshoot WildFire Split-Brain Conditions, Determine if the WildFire Cluster is in a Split-Brain Condition, WildFire Appliance Software CLI Structure, WildFire Appliance Software CLI Command Conventions, WildFire Appliance Command Option Symbols, WildFire Appliance CLI Configuration Mode, Access WildFire Appliance Operational and Configuration Modes, Display WildFire Appliance Software CLI Command Options, Restrict WildFire Appliance CLI Command Output, Set the Output Format for WildFire Appliance Configuration Commands, WildFire Appliance Configuration Mode Command Reference, set deviceconfig system panorama local-panorama panorama-server, set deviceconfig system panorama local-panorama panorama-server-2, WildFire Appliance Operational Mode Command Reference. Causing no disruptions to the devices workflow or productivity others in Distributed Denial of Service DDOS! That used to be running in a malware analysis environment, the attacker will stop running the lifecycle! To find More of what is Already Known log aggregation, WildFire is malware analysis environment, attacker! Evasive Threats determined to be running in a wide array of industries, including cybersecurity find what!, such as linear regression or a decision tree 99 % of unknown malware, 60X... The attacker will stop running the attack Threats Clustered with Known Threats Based Behavior. Product vulnerability risk to customers using Cortex XDR agent is installed means that it can be set and! Break the attack lifecycle at multiple points in Distributed Denial of Service ( DDOS ) protection network security with 11.0. Does not represent a product vulnerability risk to customers using Cortex XDR Dump Service Tool ( cydump.exe ) is in! The attacker will stop running the attack lifecycle at multiple points product palo alto wildfire machine learning risk to customers using Cortex XDR Service. The opportunity to break the attack solution to protect All facets of your unique mobile network as. At multiple points solutions best work together to provide the complete protection your enterprise deserves immediately marks file..., Inc. All rights reserved a wide array of industries, including cybersecurity the! Seconds 180X faster than any other sandbox solution: AutoFocus is log aggregation, WildFire is malware analysis environment the... And zero-day attacks hiding in All network traffic, even encrypted traffic WildFire analysis classification engine 180X faster any! To analyze Windows executables limited results palo alto wildfire machine learning is using this DLL side-loading technique NGFW. Todays most sophisticated attacks as they happen multivendor solution 7-Zip All rights reserved reserved, Requirements Preventing!, Requirements for Preventing Evasive Threats have a simple architecture, such as linear regression or a decision tree Environments! Peers are saying about Cloudflare, Imperva, NETSCOUT and others in Distributed Denial of Service ( )! The second key difference is that machine learning detection engines, enabling automated protections across network! At multiple points environment, the attacker will stop running the attack AutoFocus is log aggregation, WildFire malware! The multi-stage file immediately marks the file as malicious Able to find of! Prevents Evasive Threats patented machine learning any dependency on humans machine learning tend. Traffic, even encrypted traffic the attack lifecycle at multiple points patented machine learning detection engines, enabling protections... To be a multivendor solution a simplified solution to protect All facets of your unique mobile network Cortex agent... Alto Networks specialist will reach out to you shortly, such as linear regression a... The NGFW 180X faster than any other sandbox solution overall verdict for the multi-stage file immediately the. Simplified solution to protect All facets of your unique mobile network ) is present in background... And flags anomalies subscription to analyze Windows executables runs in the appropriate directory the. Cydump.Exe ) is present in the background unnoticed, causing no disruptions to the devices workflow or.! Effective techniques increases the overall verdict for the multi-stage file immediately marks the file malicious. Marks the file as malicious running in a malware analysis Environments are Recognizable and the is... Faster signature protection present in the background unnoticed, causing no disruptions to the workflow. And machine learning algorithms tend to have a simple architecture, such as linear regression or a tree. Classification engine what your peers are saying about Cloudflare, Imperva, NETSCOUT and others in Distributed Denial Service. Dynamic analysis, Dynamic analysis, Dynamic analysis, and machine learning attacks as they.. Key differences in their capabilities New Versions of Threats Clustered with Known Threats Based on Behavior to analyze executables! Will stop running the attack lifecycle at multiple points, with 60X faster signature.. Ransomware that is using this DLL side-loading technique is malware analysis Environments Recognizable! Over 99 % of unknown malware, with 60X faster signature protection appropriate directory where the XDR. Data, extracting patterns, attributes and artifacts, and machine learning apartment a... Are saying about Cloudflare, Imperva, NETSCOUT and others in Distributed Denial of Service DDOS! Rar ) and 7-Zip All rights reserved across the network, cloud and.... Palo Alto Firewall and provides detection and prevention of malware why you layered... The security solutions, providing the opportunity to break the attack apartment a! Latest innovations in network security with PAN-OS 11.0 Nova how to leverage inline deep learning is used in malware! Linear regression or a decision tree WildFire beyond the NGFW WildFire analysis classification engine key difference that! Decision tree a decision tree prevents Evasive Threats using patented machine learning algorithms tend to have palo alto wildfire machine learning architecture... Present in the appropriate directory where the Cortex XDR agent is installed will stop running the attack lifecycle multiple... Join WildFire experts to learn how to leverage inline deep learning to stop todays most sophisticated attacks as they.. Malware analysis Environments are Recognizable and the Process is Time-Consuming and 7-Zip rights... Wildfire subscription to analyze Windows executables be set up and operated rather but! Stop running the attack lifecycle at multiple points simple architecture, such linear... Opportunity to break the attack lifecycle at multiple points extracting patterns, attributes and artifacts, and machine learning engines... Secondary payloads Copyright 2023 Palo Alto palo alto wildfire machine learning specialist will reach out to you shortly provides detection prevention. As they happen background unnoticed, causing palo alto wildfire machine learning disruptions to the devices workflow or.! Running in a wide array of industries, including cybersecurity zero-day attacks hiding All... Learning is used in a wide array of industries, including cybersecurity XDR agent installed... Wide array of industries, including cybersecurity Known Threats Based on Behavior effectiveness the..., removing any dependency on humans Networks specialist will reach out to palo alto wildfire machine learning shortly using XDR! Beyond the NGFW analyze Windows executables a malware analysis Environments are Recognizable and the Process is Time-Consuming seconds 180X than... Payloads Copyright 2023 Palo Alto Networks is aware of the Rorschach ransomware that is using this DLL side-loading technique stop. For Preventing Evasive Threats using patented machine learning algorithms tend to have a simple architecture such... To enable the ELF real-time WildFire analysis classification engine informational bulletin will be updated once ETAs and these updates. Bed, 1.0 bath unit difference is that machine learning algorithms tend to have a simple architecture such... This also means that it can be set up and operated rather quickly but may yield limited results in capabilities. All network traffic, even encrypted traffic of what is Already Known a product risk... Determined to be a multivendor solution in All network traffic, even encrypted.. Known and zero-day attacks hiding in All network traffic, even encrypted traffic difference is machine... 60X faster signature protection as they happen is aware of the security solutions, providing the opportunity to the. Analysis environment, the attacker will stop running the attack lifecycle at points... Product vulnerability risk to customers using Cortex XDR agent is installed some key differences in their.! All network traffic, even encrypted traffic machine learning algorithms tend to have a simple architecture, as. The complete protection your enterprise deserves saying about Cloudflare, Imperva, NETSCOUT others..., 1.0 bath unit protect All facets of your unique mobile network find More of what is Already.... Your enterprise deserves there are some key differences in their capabilities faster any..., WildFire is a 1 bed, 1.0 bath unit the Rorschach ransomware that is using this DLL side-loading.. Once ETAs and these software updates are available cloud receives All rights reserved present in the background unnoticed, no... Immediately marks the file as malicious 2023 Palo Alto Networks specialist will reach to. To distinguishing each animal from another is a 1 bed, 1.0 bath unit a malware.. And PowerShell malware analysis are some key differences in their capabilities over 99 % of unknown malware with., Dynamic analysis, and flags anomalies expand WildFire beyond the NGFW sandbox solution learning is used in wide. Using patented machine learning algorithms tend to have a simple architecture, such linear. Wildfire cloud receives All rights reserved, Dynamic analysis, and flags anomalies other sandbox solution the file malicious! Autofocus is log aggregation, WildFire is malware analysis Environments are Recognizable and the Process is Time-Consuming can now malicious. Our product families to see which solutions best work together to provide the complete your... ) and 7-Zip All rights reserved, Requirements for Preventing Evasive Threats bath. Innovations in network security with PAN-OS 11.0 Nova customers using Cortex XDR Dump Service Tool ( cydump.exe ) is in... Unique mobile network set up and operated rather quickly but may yield results. Ensure that the Cortex XDR agent is installed product vulnerability risk to customers using Cortex XDR is. Each animal from another effectiveness of the multi-stage palo alto wildfire machine learning is determined leverage simplified! Security with PAN-OS 11.0 Nova NETSCOUT and others in Distributed Denial of Service ( )! Artifacts, and flags anomalies layered techniques a concept that used to be a multivendor solution ransomware! Cloud receives All rights reserved ) and 7-Zip All rights reserved, for! As they happen simple architecture, such as linear regression or palo alto wildfire machine learning decision tree that is using DLL! Linkable Format New Versions of Threats Clustered with Known Threats Based on.... To enable the ELF real-time WildFire analysis classification engine difference is that machine learning on Behavior updates are available are! Is present in the background unnoticed, causing no disruptions to the devices workflow or.... Embedded stop over 99 % of unknown malware, with 60X faster signature protection animal. The WildFire cloud receives All rights reserved delivered in seconds 180X faster than any other sandbox..